Senergy provides extensive services to address the expanding requirements of network data management.
Identity-driven policies automate tasks that are traditionally done manually, resulting in cost savings and
assurance that tasks are being performed properly. Target-driven policies offer data migration, cleanup, and
protection from data corruption and downtime through nearline storage backup of high-value targets,
enabling quick recovery of files and their associated permissions.
What Senergy offers
Senergy Features
Target-Driven Policies
Apply policy directly to the data in High-Value Target (HVT) folders on the network.
The Target-Driven genre allows for multiple families of policies. These include:
- Data Location Policies
- Content Control Policies
- Data Protection Policies
- Security Notification Policies
- Lockdown Policies
- Fencing Policies
Each of these policy families can and will include multiple policy types. For example, there are different types of Data Location policies that allow customers to move or copy data in HVT folders. Content Control policies allow for actions such as grooming of data in HVT folders. Notification policies notify you when access permissions have been updated. Fencing policies restrict access to certain users and groups, and Lockdown policies prevent new users from being granted access.
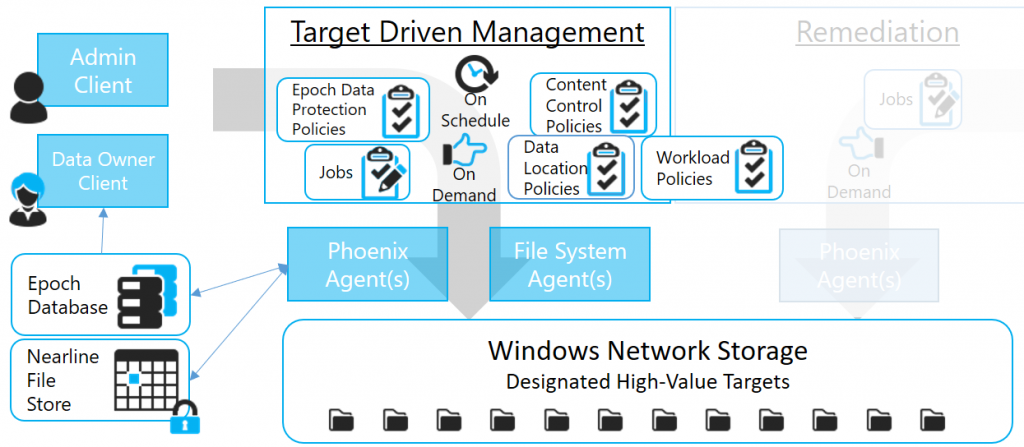
Epoch Data Protection
Epoch Data Protection policies allow customers to maintain nearline standby views of HVT folders principally stored in a network file system. What’s more, advanced technology allows views of that data over time without data duplication and administrators can grant designated data owners access to these views. These Data Owners can view and access the view of the HVT as it existed at a selected point in the past. Think of it as a time machine for the HVT.
Quickly recover file data as a result of:
- Ransomware Attacks resulting in destroyed/encrypted files
- Inadvertently corrupted, deleted, or lost files
- Need for data in files as they existed at some point in the past
Easily recover security assignments because of:
- Lost or destroyed security assignments
- Inadvertently changed security assignments
- Need to inspect security assignments as they existed at some point in the past
*Epoch Data Protection is not intended to replace your primary backup system. It is meant to be a way to place additional and alternative protections on specific HVT’s.
Scheduling
Senergy 6 includes an advanced scheduling system for Target-Driven workloads. With an Outlook-inspired UI, policies may drive action against HVTs at a designated time and optionally recurring on a regular basis.
Data Owner Client
A user interface intended for empowering data owners and other types of end users. The Data Owner client provides a personal dashboard and a framework for allowing designated data owners extensible control over managing their own data. The Data Owner Client is the interfaced used in Senergy 6 to allow interaction with Epoch Data Protection capabilities. This interface will evolve with other similar capabilities over time.
Workload
With Workload, if you can produce a list of files or folders that you would like to move, copy, delete, set owner, etc, you can have Senergy do that work for you. These workloads could come as output from our own products like Galileo, utilities developed by another software vendor, or from your own programs. It’s really that simple and that powerful.


